
I am a huge fan of using precise AWS IoT Policies. To make them flexible yet restrictive I heavily use the IoT Policy Variables.
Unfortunately, putting all of those best practices in place lead to:
❌ Deployment failed: Error: Stack Deployments Failed: Error: The stack named GGMainInfra failed creation, it may need to be manually deleted from the AWS console: ROLLBACK_COMPLETE: Resource handler returned message: "Invalid request provided: Policy cannot be created - size exceeds hard limit (2048)
I exceeded the allowed IoT Policy size which is 2048 characters (excluding white spaces). What is worth mentioning is that is the non-adjustable limit, so we need to have some way to work around it.
In my case, I wanted to define a restrictive IoT Policy for Greengrass and Client Devices (devices interacting with Greengrass installed at the edge via the local network).
I decided to split my IoT Policy into two distinct policies:
- IoT Policy required for the Greengrass Device to operate
- IoT Policy enabling communication between the Greengrass Device and Client Devices
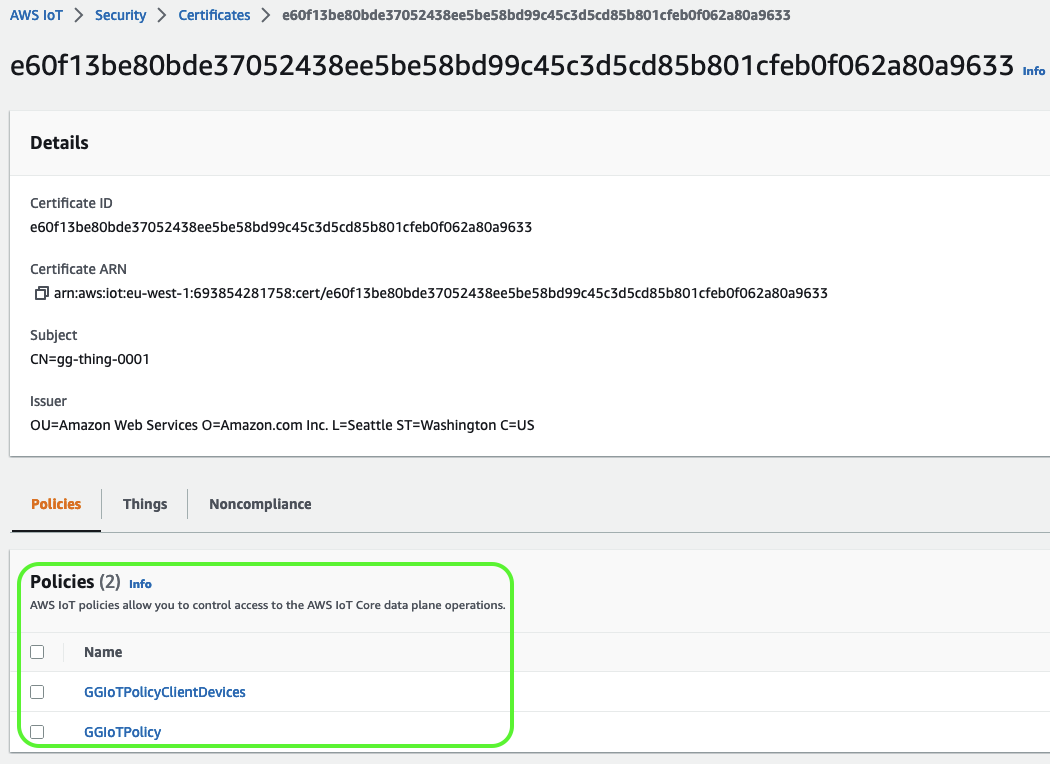
This way both of my IoT Policies fit into the 2048 characters limit. But there was an even bigger gain of this separation.
Every IoT Policy defines only actions required for a specific task which makes them easier to verify and debug potential access issues. A single huge policy would make it hard to track all actions.
There is a hard limit to the number of IoT Policies that can be attached to a single Certificate - we can use a maximum of 10 IoT Policies.
I’ve got an idea regarding the workaround for this limit once I hit it, but that is a topic for another post :)

