The beauty of using certificates - Strengthen Your IoT Security!
While passwords might have served us in simpler times, the IoT era calls for something more secure and inherently reliable - the x.509 Certificates.
Why the Shift to x.509 Certificates?
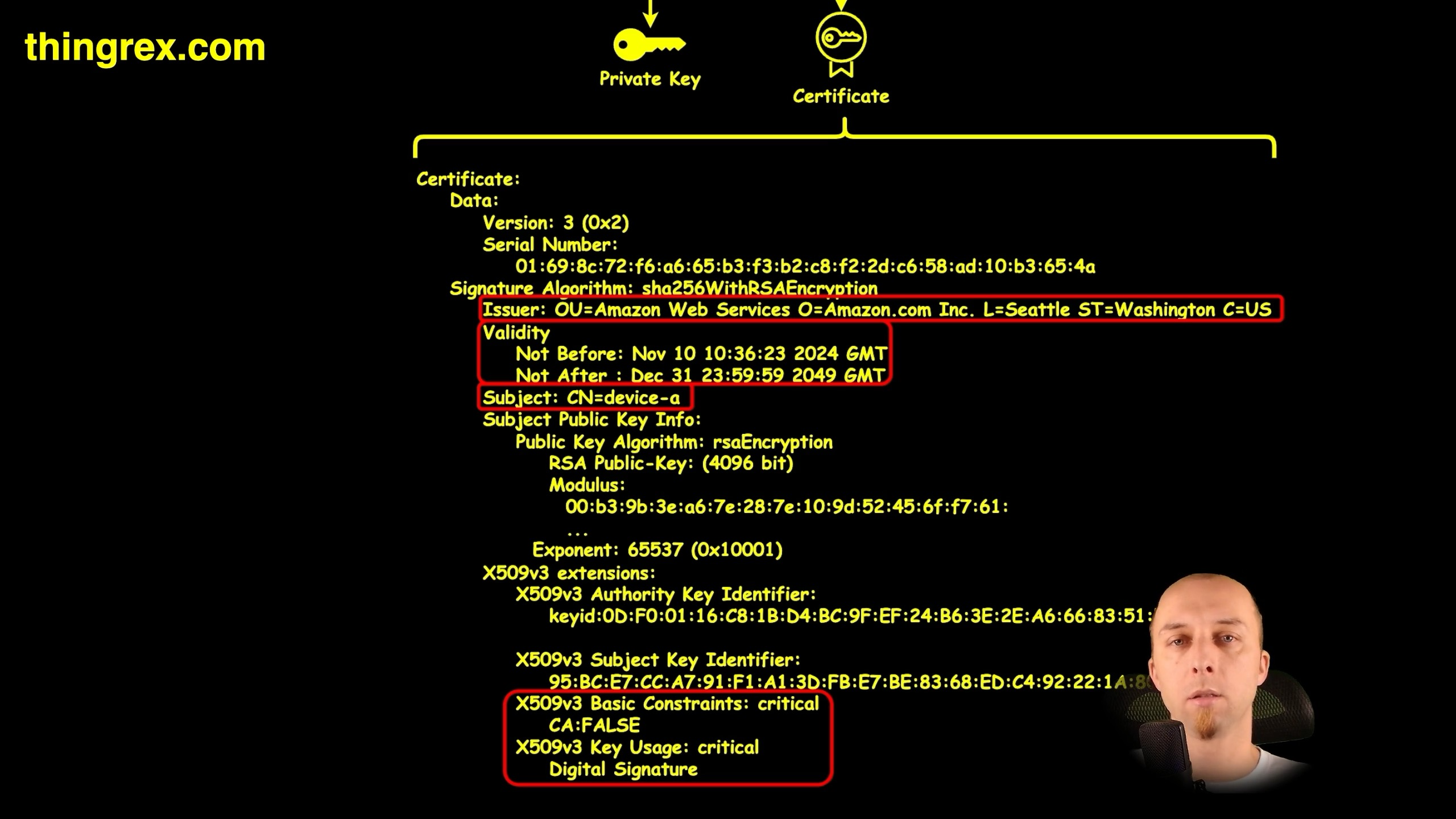
✅ Built-In Trust: Each certificate is issued by a trusted authority (like AWS). If you trust the issuer, you automatically trust the certificate and the device it represents. That reduces complexity and establishes a direct, verifiable chain of trust.
✅ Identity in the Certificate Itself: Unlike a password, where identity hinges on an external database lookup, a certificate carries the device’s identity right inside it.
✅ Time-Sensitive Validity: Passwords don’t age gracefully on their own. Certificates do. Each x.509 Certificate comes with a clearly defined validity period. When it expires, it’s no longer valid - simple as that. It’s another built-in security measure that ensures you don’t rely on outdated credentials.
✅ Defined Usage Context: Certificates also outline how they’re supposed to be used. This “key usage” attribute means there’s less guesswork and fewer opportunities for misuse. Think of it as an instruction manual directly embedded into the credential.
When you deploy IoT devices at scale, managing identities securely and efficiently is non-negotiable. x.509 Certificates provide a self-contained, extensible, and trust-driven framework that goes beyond the old username-and-password approach.
Ready to ditch the old-school credentials and embrace a more secure future? Now is the time to elevate your IoT identity management with x.509 Certificates.
👍 Thumbs up if you are using the x.509 Certificates in your system!
